Task 2
Configure an IP standard ACL that denies packets coming from the host 172.31.123.3 going towards 192.168.5.0/24. Traffic from other sources should be allowed.
Again, we use the standard IP ACL here, which is going to be applied on R5. Here goes:
R5 Configuration:
!
! In the global config
!
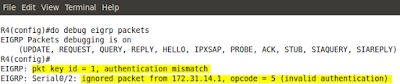
access-list 1 deny host 172.31.123.3
access-list 1 permit any
!
! Enter the the incoming interface and apply the access-list
!
interface serial0/2
ip access-group 1 in
!
Notice!
- access-list 1 - ACL numbers 1-99 are IP standard ACLs (check source of the packets only.
- host 172.31.123.3 - this keyword is an alias for: 172.16.123.3 0.0.0.0. It is a source address of the packets being inspected.
- any - this keyword is an alias for: 0.0.0.0 255.255.255.255 - any source here.
First, look at the syntax you see in Cisco documentation:
Pic. 1 - Extended ACL Syntax.
The options we are going to use can be presented as follows:
Pic. 2 - Extended ACL Common Syntax.
The best way to explain the syntax you need to get familiar with is to use an example and try to de-construct it. So, let's look at our topology one more time and create the following filter:
Task 1
Deny telnet sessions coming from 192.168.4.0/24 destined to 172.31.3.0/28 and 172.31.3.16/28. All other traffic should be allowed.
Pic. 3 - Topology.
Icons designed by: Andrzej Szoblik - http://www.newo.pl
Which ACL type should we use?
Since, we are very specific in terms of which protocols we want to deny, we must use Extended ACL. The standard ACL can only match on the source IP address, permitting or denying all protocols the packet is carrying.
Which router/interface should we apply the ACL on?
Our topology clearly shows that R3 has three different interfaces with three different addresses. So, we have two options here:
- We can configure an Extended ACL on R4 FastEthernet 1/0 interface in the inbound direction (close to the source as per ACL guideline)
- We can configure an Extended ACL on R4 Serial0/2 in the outbound direction.
- Alternatively, we can apply an Extended ACL on R3 FastEthernet1/0 (inbound).
Let's read the task again:
Task 1
Deny telnet sessions coming from 192.168.4.0/24 destined to 172.31.3.0/28 and 172.31.3.16/28. All other traffic should be allowed.
Here's one way to configure this:
R4 Configuration:
!
! In the global 'config' mode the statements are:
!
access-list 100 deny tcp 192.168.4.0 0.0.0.255 172.31.3.0 0.0.0.15 eq 23
access-list 100 deny tcp 192.168.4.0 0.0.0.255 172.31.3.16 0.0.0.15 eq 23
access-list 100 permit ip any any
!
! Apply the ACL on the interface
!
interface Serial0/2
ip access-group 100 out
!
Three lines that 'deny' traffic are similar. Let's dissect its syntax:
access-list 100 deny tcp 192.168.4.0 0.0.0.255 172.31.3.0 0.0.0.15 eq 23
- access-list 100 - The extended ACL (numbers 100-199)
- deny - condition (either 'deny' or 'permit' are allowed)
- tcp - layer 3 or 4 protocol (such as: ip, icmp, tcp, udp, rip, eigrp etc.)
- 192.168.4.0 - source IP address
- 0.0.0.255 - source wildcard mask (inversed mask)
- 172.31.3.0 - destination IP address
- 0.0.0.15 - destination wildcard mask (inversed mask)
- eq - operator: eq (equal), lt (less than), gt (greater than), range
- 23 - destination port (telnet)
After source wildcard there is no source port. This means that the source port is not inspected at all (disregarded).
In the next post I'm going to show you few examples of extended ACL which should reinforce your study (today I have a friend over from UK so no time to do it ;))